Maureen Data Systems
Application & Device Security
Simple Setup
Deploy security across your devices, and use automated built-in intelligence to rapidly protect, detect, and respond to threats.
Increased Efficiency
Leverage streamlined onboarding and management experiences that provide actionable insights for fast and easy use.
Cost Effective
Designed to deliver comprehensive security value at a price point that works for your business.

What is Application Security
Application security describes security measures at the application level that aim to prevent data or code within the app from being stolen or hijacked. It encompasses the security considerations that happen during application development and design, but it also involves systems and approaches to protect apps after they get deployed.
Application security may include hardware, software, and procedures that identify or minimize security vulnerabilities. A router that prevents anyone from viewing a computer’s IP address from the Internet is a form of hardware application security. But security measures at the application level are also typically built into the software, such as an application firewall that strictly defines what activities are allowed and prohibited. Procedures can entail things like an application security routine that includes protocols such as regular testing.
Why It's important
Application security is important because today’s applications are often available over various networks and connected to the cloud, increasing vulnerabilities to security threats and breaches. There is increasing pressure and incentive to not only ensure security at the network level but also within applications themselves. One reason for this is because hackers are going after apps with their attacks more today than in the past. Application security testing can reveal weaknesses at the application level, helping to prevent these attacks.


Application Security Types
Different types of application security features include authentication, authorization, encryption, logging, and application security testing. Developers can also code applications to reduce security vulnerabilities.
Authentication: When software developers build procedures into an application to ensure that only authorized users gain access to it. Authentication procedures ensure that a user is who they say they are. This can be accomplished by requiring the user to provide a user name and password when logging in to an application. Multi-factor authentication requires more than one form of authentication—the factors might include something you know (a password), something you have (a mobile device), and something you are (a thumb print or facial recognition).
Authentication: When software developers build procedures into an application to ensure that only authorized users gain access to it. Authentication procedures ensure that a user is who they say they are. This can be accomplished by requiring the user to provide a user name and password when logging in to an application. Multi-factor authentication requires more than one form of authentication—the factors might include something you know (a password), something you have (a mobile device), and something you are (a thumb print or facial recognition).
Encryption: After a user has been authenticated and is using the application, other security measures can protect sensitive data from being seen or even used by a cybercriminal. In cloud-based applications, where traffic containing sensitive data travels between the end user and the cloud, that traffic can be encrypted to keep the data safe.
Logging: If there is a security breach in an application, logging can help identify who got access to the data and how. Application log files provide a time-stamped record of which aspects of the application were accessed and by whom.
Application security testing: A necessary process to ensure that all of these security controls work properly.
Application Security in the Cloud
Application security in the cloud poses some extra challenges. Because cloud environments provide shared resources, special care must be taken to ensure that users only have access to the data they are authorized to view in their cloud-based applications. Sensitive data is also more vulnerable in cloud-based applications because that data is transmitted across the Internet from the user to the application and back.
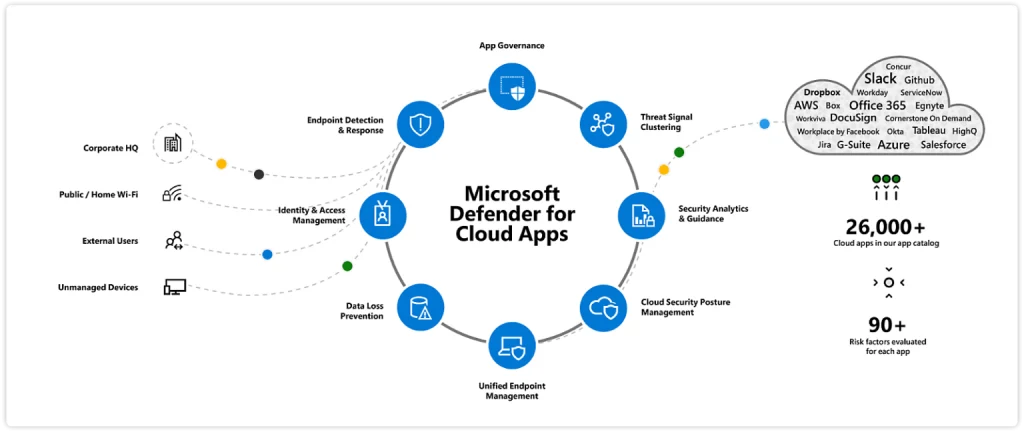

Mobile Application Security
Mobile devices also transmit and receive information across the Internet, as opposed to a private network, making them vulnerable to attack. Enterprises can use virtual private networks (VPNs) to add a layer of mobile application security for employees who log in to applications remotely. IT departments may also decide to vet mobile apps and make sure they conform to company security policies before allowing employees to use them on mobile devices that connect to the corporate network.
Web Application Security
Web application security applies to web applications—apps or services that users access through a browser interface over the Internet. Because web applications live on remote servers, not locally on user machines, information must be transmitted to and from the user over the Internet. Web application security is of special concern to businesses that host web applications or provide web services. These businesses often choose to protect their network from intrusion with a web application firewall. A web application firewall works by inspecting and, if necessary, blocking data packets that are considered harmful.


Secure Mobility Services
It helps organizations secure critical systems and sensitive information to avoid digital attacks, both external and internal.
Through deploying our Secure Mobility Services among enterprises and government organizations, we are able to help them regulate the people involved in all transactions. Risks arise from clients, to employees, to contractors, up to the c-levels.
Our goal is to enable organizations get the benefit of combatting threats against network systems & applications, and the seamless access of people to systems and information.
We help organizations provide their people with high level productivity experiences through enabling them access mobile apps such as Outlook, Word, Excel and PowerPoint. Enterprise Mobility seamless and without fear of threats, without affecting the personal data and without the need of enrolling every device for management.






Client Testimonials
Maureen Data Systems
Why Choose Us?

Strategy
We meet you where you are in your technical journey to develop a roadmap for success.

Execution
We deliver end-to-end IT and digital transformation solutions across different ecosystems.

Continuity
We ensure operational readiness and transition you from projects to managed services seamlessly.
